1 Kernun Adaptive Firewall
Kernun Adaptive Firewall is a modern tool for monitoring and controlling network traffic. It uses a unique database of current threats and updates it continuously. Thanks to that, it provides continual defense even against currently active attacks.
2 Deployment
This chapter contains information needed for deploying and connecting Kernun Adaptive Firewall to network. Installation options and possible deployment modes are described here and the chapter ends with describing logging into the user interface and making a simple network configuration.
2.1 Installation
The company Trusted Network Solutions provides three options for Kernun Adaptive Firewall installation. These options are having Kernun Adaptive Firewall preinstalled by the Kernun technical support, installation with the usage of default values and installation without the usage of default values.
2.1.1 Preinstallation by Kernun technical support
The first option of Kernun Adaptive Firewall installation is to let Kernun technical support to install it and configure it. This option is available for hardware machines as well as for virtual appliances. The customer delivers the expected configuration (e.g. expected addresing) and technitians install Kernun Adaptive Firewall on the device and cofigure it according to expectations. After that, the device is connected into the customer's network and starts working immediately.
2.1.2 Installation with default values
The second option of Kernun Adaptive Firewall installation is an independent installation by a customer to whom the installation disk is delivered. The installation runs automatically and default values will be used. These values depend on the selected deployment mode (Deployment modes) and are described in tables below.
| Web proxy gate | |
|---|---|
| Network interface address | 192.168.1.2/24 |
| DNS server address | 1.1.1.1 |
| Default gateway address | 192.168.1.1 |
| Perimeter firewall | |
|---|---|
| LAN interface address | 192.168.1.2/24 |
| Hostname of the device | Kernun |
| Domain | int |
After the installation and restart of the device, it is possible to connect to the user interface (Login) and make any eventual configuration changes.
2.1.3 Installation without default values
The last variant of Kernun Adaptive Firewall installation is an independent installation by a customer during which default values are not used. With this type of installation, physical access to the device's terminal is needed. Similarly to the installation with default values, the installation medium is delivered to the customer and the installation itself is automatic. After the installation and a restart of the device, it is necessary to log in to the terminal of the device with username sysadmin and password sysadmin. Then a commandadmin conf-reinitneeds to be ran. This command guides through basic settings of Kernun Adaptive Firewall. Then, it is possible to log in to the user interface.
2.2 Deployment modes
Kernun Adaptive Firewall can be deployed in several modes. These are Perimeter firewall, Web proxy gateway and Transparent firewall. Each deployment mode is intended for a different use case but there are some settings common for all modes.
2.2.1 Perimeter firewall
Kernun Adaptive Firewall can be connected to the network as a perimeter firewall. It represents an implementation of a perimeter firewall that connects two or more networks with different levels of trust. Typically, it is used for connecting a private network to the Internet and providing a high level of security. The default settings of security policy are that immediately after connecting the device to the network all safe traffic from the LAN network is allowed and all traffic initiated from the Internet is blocked.
In this deployment mode, Kernun Adaptive Firewall provides all services which can be expected from a perimeter router such as VLAN definition, static routing settings or DHCP server.
This deployment mode supports joining two devices into a cluster for achieving high availability. To make a cluster, two separate nodes need to be installed first. They are then connected into a cluster by following a guide in the user interface (more information in the cluster section).
2.2.2 Web proxy gateway
Kernun Adaptive Firewall can be connected to the network as a web proxy gateway. In this deployment mode the device is connected to the network as any other machine or server and provides an access to web pages of the Internet to the LAN network, so called HTTP proxy. It allows the customer to filter web traffic according to security policy, to force user authentication, to do TLS inspection or to disable tunneling.
In the web proxy gateway deployment mode, similarly to the perimeter firewall, there are many auxiliary services like VLAN definition or DHCP server.
2.2.3 Transparent firewall
In the transparent firewall deployment mode, Kernun Adaptive Firewall is connected to the network without a need to change current network topology of the customer. In this case, the device is connected to the network as a network bridge through which all the traffic goes, and which is invisible for users. In this deployment mode, adaptive firewall is the main security feature.
2.3 The first login
After the device installation, it is possible to log in to the user interface. Access to the interface is provided via web browser that is used to connect to the IP address or hostname of the device securely by using HTTPS protocol. In case of a device with multiple network interfaces, any address of the device can be used. After typing the address, the login screen is loaded.
2.3.1 Default user
Right after the installation, Kernun Adaptive Firewall contains one default user. It is an administrator user that has username admin and password admin. After the login screen is loaded, it is possible to change the language of the interface, type the name and the password into their respective fields and log in. Right after the first login with the default username and password, a window with password change prompt is shown. This means that logging as a admin with the default password is possible only once after the installation.
2.3.2 Network settings
If the installation with default values was used (Installation) and some changes to the network settings are needed, the user should do so after the first logging in into the user interface. Network settings take place in the section.
3 User interface
For administration, Kernun Adaptive Firewall provides a graphical user interface which is accessible from a web browser. If not specified otherwise in stateful firewall (Stateful firewall), the user interface is available on all IP addresses of all physical interfaces and can be accessed from the hostname as well. The interface itself consist of multiple main parts that are explained in this chapter.
3.1 Navigation
The user interface is navigated through a menu in the left part of the screen. The menu is split into sections, each one containing subsections relevant to the superior section. In the bottom of the menu, there is a user section which allows profile management of the currently logged in user and physical actions with the machine, such as turning the machine off or restarting it.
For smaller screens, there is a button Hide menu in the upper part of the menu, which can minimize the menu.
3.2 Main window
The largest part of the user interface is taken by the main window. It is split to a smaller, comprehensive cards according to content. Every card contains information, configuration items and data regarding one topic.
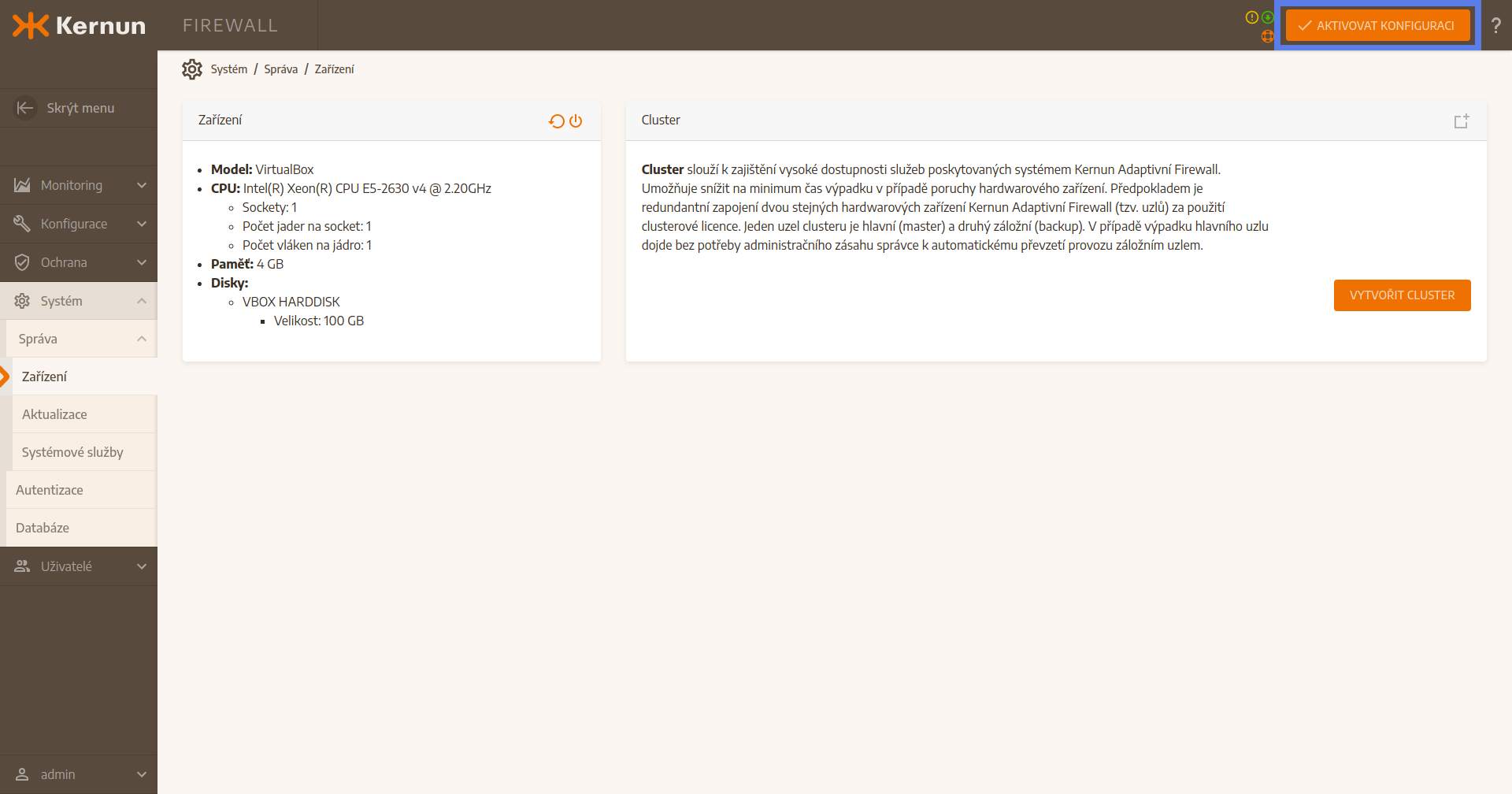
3.3 Configuration activation
In the top right corner of the user interface there is an orange button Activate the configuration. It is used to execute configuration activation which is needed for application of some changes. More about configuration activation can be found in section link cfgActivation.
3.4 State of the device
To the left of the Activate the configuration button, there are icons which signal the state of the device. Some only have informational purpose, e.g. system readinesss for an update, others point out problems, e.g. an outdated database, a not-running system services and so on.
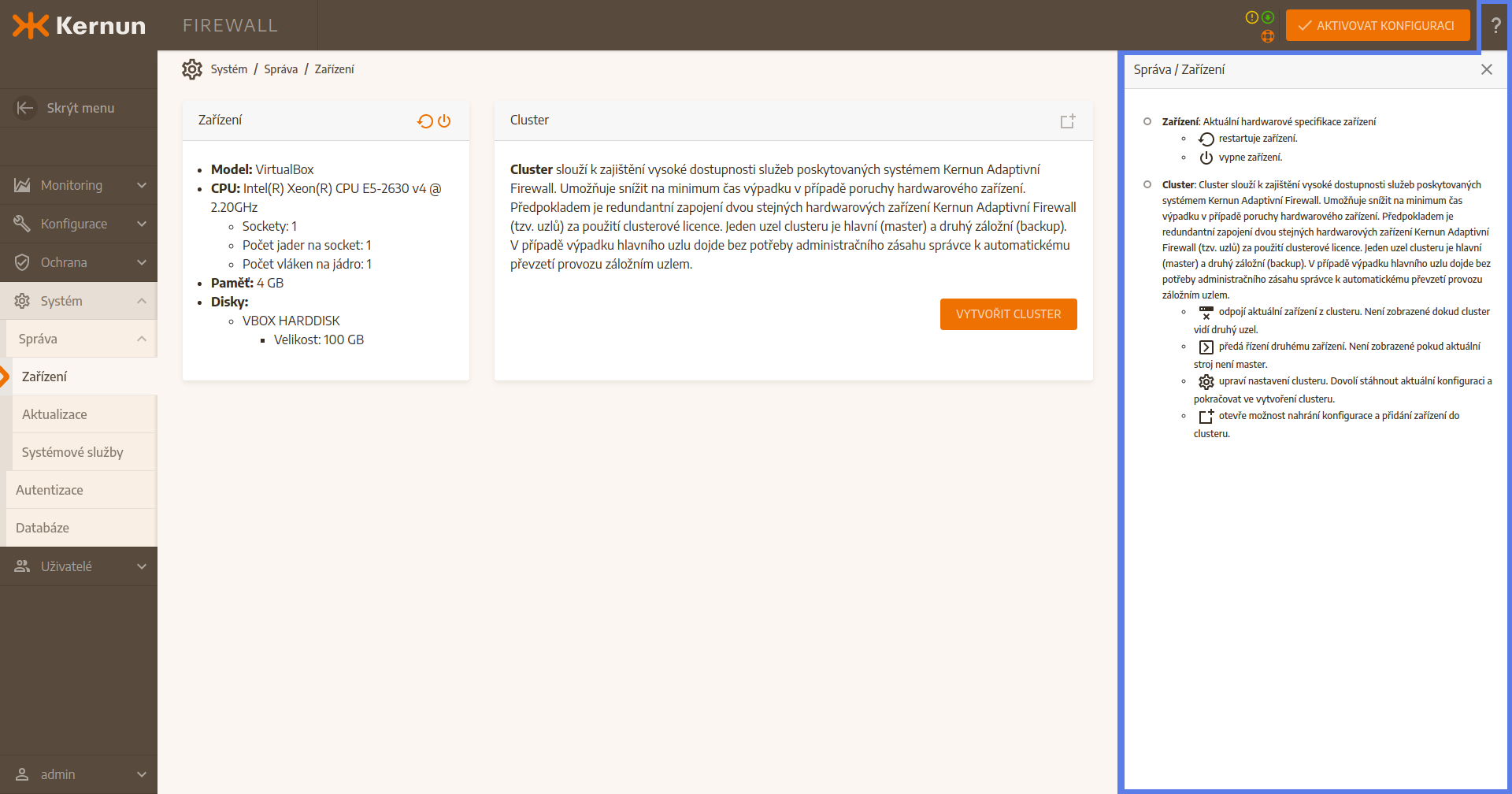
3.5 Help
On the right hand side of the Activate the configuration button, there is a question mark shaped button. After pressing it, a comprehensive help window is opened on the right side of the screen. This window contains explanation of every item of the user interface. Only the help for the current section is displayed. That means that for displaying for example a stateful firewall help page (Stateful firewall), it is necessary to be in section Stateful firewall.