The idea behind honeypot is to provide a resource valuable to attacker and by monitoring attackers behaviour counteract his attempts to unauthorized use of information systems. In an example scenario, we dedicate one public IP adress as "honeypot" address. This IP address should not be referred in any DNS record and must not by referred in any web site or elsewhere, so that we can assume only attackers automatically scanning all IPs attempts to connect to this honeypot address. Automatic scans function generally in two modes. Some scanners send TCP SYN packets to a range of IP addresses, immediately forgeting about it a detecting open ports by simply monitoring incomming TCP SYN+ACK packets (see http://en.wikipedia.org/wiki/Transmission_Control_Protocol#Connection_establishment for explanation of TCP connection establishment). Other scanners attempts to complete TCP handshake and eventually continue the scan on application level. Kernun UTM logs all attempts to connect to honeypot and blacklists all IP addresses that completed TCP handshake. Once on blacklist, any traffic (any protocol) on any network interface (not just honeypot address) from that IP address is blocked.
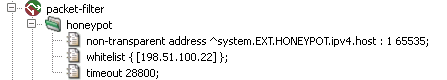
The section honeypot is part of the
packet-filter. The item non-transparent
defines on which address and ports should we listen for attacker's connections.
In this example it's all available ports. In whitelist
we defined IP address of our monitoring server which should not be placed
on blacklist even if it connects to honeypot address. Finally
timeout defines time period (in seconds) for which IP address
should remain in blacklist, after it became silent, i.e. after there is no
new connection from that IP address on any of our network interfaces.