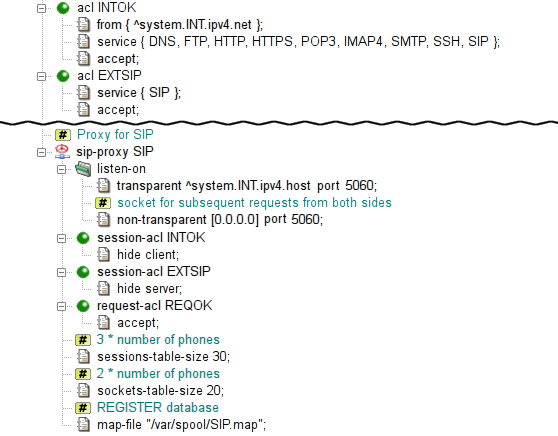
sip-proxy is the proxy daemon
for the Session Initiation Protocol (RFC 3261 et al.),
i.e. mainly Internet telephone calls and related services.
The proxy is configured in the sip section.
In the sample configuration depicted in Figure 5.35, “SIP Proxy”,
chroot-dir defines directory into which it should be chrooted.
The proxy listens transparently for requests at Kernun UTM's internal address
at port 5060. However, due to the hop-by-hop logic of the protocol,
the proxy must listen on this port non-transparently
on all internal and external interfaces as well.
As usually, the proxy must be referenced by at least one ACL in the
system section. In order to enable incoming calls,
we will need to allow also sessions from the external network.
sip-proxy uses two-phase ACLs. The first phase,
session-acl, is checked once for each client connection.
It permits or denies client access and sets some connection parameters.
This is where the administrator can specify that some important data
that is usually stored in SIP messages headers (e.g. internal addresses)
is to be hidden.
The second phase, request-acl, is checked once for
each request and it can be used e.g. to change the target server
according to the Request-URI.
sip-proxy requires specification of the maximum
of sessions and data channels used in parallel.
An estimate is three times number of the phones
for sessions-table-size
and two times number of the phones
for sockets-table-size.
Finally, the proxy requires a file to store the registration data
of clients (local phones).
The complete resulting configuration can be found
in /usr/local/kernun/conf/samples/cml/sip-proxy.cml.
See sip-proxy(8) and sip-proxy(5) to learn more about sip-proxy.