In the first section of this chapter, we will introduce the principles of
the Kernun UTM configuration. We will describe the syntax and semantics of the
configuration language and its two different representations. The textual
representation is used in the configuration file (usually
/usr/local/kernun/conf/kernun.cml) and by the command
line configuration tool
cml(8). The graphical representation is used
by the Kernun GUI. Then we will discuss the initial
configuration that is generated when the newly installed Kernun UTM is booted for
the first time. We will explain the meaning of individual items in this
configuration and how to change them. For information about configuration of
additional functionality not included in the initial configuration, such
as more types of proxies, authentication, antivirus, or antispam
modules, refer to Chapter 5, Advanced features.
Kernun UTM keeps its configuration in a text format called CML
(Configuration Meta Language). The configuration is usually stored in the
/usr/local/kernun/conf/kernun.cml file. Whenever the
configuration file is saved by the GUI or command line tools, it is also saved
to a RCS (Revision Control System) file called
/usr/local/kernun/conf/kernun.cml,v. The RCS file contains
the complete history of the configuration, which makes it possible to return to
any past version of the configuration file, show differences between two versions,
and more. The Kernun GUI and
cml(8) provide functions for work with RCS
files. For more advanced operations with RCS, you can use command line system
tools, see rcsintro(7).
Speaking more precisely, there are two levels of configuration: high and low. Usually, the administrator maintains only the high-level configuration file. On the other hand, each Kernun UTM component reads its low-level configuration file upon starting. The Kernun UTM configuration handling tools generate a set of low-level configuration files[17] from the single high-level configuration file. In fact, the high-level configuration is more or less an extension of the low-level configuration of proxies. This concept makes it possible to keep a simple configuration file for each proxy and, at the same time, maintain a single file that describes the whole system in a comfortable way.
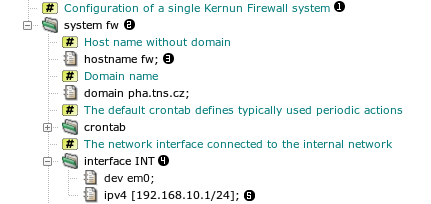
The configuration has a tree structure consisting of sections, items, and elements. A section is a named group of logically connected configuration directives. It can contain other (sub)sections and items. An item is a named group of values—elements. The configuration structure is reflected by the view of the configuration in the GUI, see Figure 4.1, “Tree structure of the configuration”, as well as in the corresponding textual configuration file:
## Configuration of a single Kernun UTM systemsystem fw {
## Host name without domain hostname fw;
## Domain name domain pha.tns.cz; ## The default crontab defines typically used periodic actions crontab { $DEFAULT-CRONTAB; } ## The network interface connected to the internal network interface INT {
dev em0; ipv4 [192.168.10.1/24];
}
In the sample configuration there is a section of type system
named fw  . It contains several
subsections and items. For example, an item
. It contains several
subsections and items. For example, an item hostname with
an element (value) fw  , or
a subsection
, or
a subsection interface named INT  containing
an item
containing
an item ipv4  . Note that it is
possible to include comments in the configuration file. They are also
displayed by the GUI
. Note that it is
possible to include comments in the configuration file. They are also
displayed by the GUI  .
.
Nodes of the configuration tree are referenced by
paths. A path lists the ancestor sections in the tree. In
the above example, the fw.INT.ipv4 path denotes the item  . Instead of specifying a value for an element, it is
possible to use a reference to another value in the configuration with the
same type. For example, the initial configuration contains
. Instead of specifying a value for an element, it is
possible to use a reference to another value in the configuration with the
same type. For example, the initial configuration contains
Here,  denotes the value obtained by going up
the tree to the
denotes the value obtained by going up
the tree to the system type node (section
system fw), and then down to the node named
INT (it is interface INT), then to
ipv4, and finally we take its host element
(value).
References ensure the consistency if the same value appears at two or
more places in the configuration. If the same path is to be repeated
several times, e.g., in listen-on of several proxies, we
may avoid the use of the full path by using a
variable.
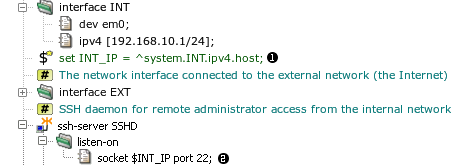
system fw {
interface INT {
dev em0;
ipv4 [192.168.10.1/24];
}
set INT_IP = ^system.INT.ipv4.host;  ...
## SSH daemon for remote administrator access from the internal network
ssh-server SSHD {
listen-sock $INT_IP
...
## SSH daemon for remote administrator access from the internal network
ssh-server SSHD {
listen-sock $INT_IP  : 22;
passwd-auth;
}
: 22;
passwd-auth;
}
The previous example is changed so that the reference path is stored in a
variable called INT_IP  and the
variable is used instead the full path later
and the
variable is used instead the full path later  .
For the GUI view of the same configuration, see Figure 4.2, “Tree structure of the configuration”.
In addition to these data variables it is possible to
define variables containing several configuration items or even whole
sections. These section variables can be parametrized.
A simple example of section variables will be shown in the next paragraph,
along with file includes.
.
For the GUI view of the same configuration, see Figure 4.2, “Tree structure of the configuration”.
In addition to these data variables it is possible to
define variables containing several configuration items or even whole
sections. These section variables can be parametrized.
A simple example of section variables will be shown in the next paragraph,
along with file includes.
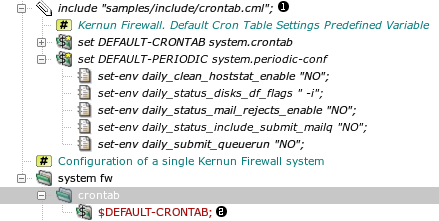
A configuration file can include another file. After
the installation there are several include files in
/usr/local/kernun/conf/samples/include. The initial
configuration includes two of them, root-servers.cml (a
list of root DNS servers) and crontab.cml (the default
configuration of the
cron
(8) daemon that runs
periodic actions in the system, e.g., log rotation). Example: the
crontab.cml include file contains
set DEFAULT-CRONTAB system.crontab {
...
}
set DEFAULT-PERIODIC system.periodic-conf {
set-env daily_clean_hoststat_enable "NO";
set-env daily_status_disks_df_flags " -i";
set-env daily_status_mail_rejects_enable "NO";
set-env daily_status_include_submit_mailq "NO";
set-env daily_submit_queuerun "NO";
}
It is included in the main configuration file kernun.cml
include "samples/include/crontab.cml";
...
system fw {
...
crontab {
$DEFAULT-CRONTAB;
}
The same excerpt of the configuration viewed in the GUI is shown in Figure 4.3, “Including configuration files and using section variables”.
The crontab.cml file is included at
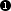
DEFAULT-CRONTAB and
DEFAULT-PERIODIC. The first variable is used
at 
Configuration elements are of various types. All the types and their exact syntax are described in configuration(7). Here we only list the types and present the most important syntax rules.
Integers — a nonnegative decimal or hexadecimal value; several types with different numbers of bits
Port number — an integer or a service name from
/etc/servicesString — a sequence of characters in double quotes. It is possible to omit the quotes for strings that contain only a limited set of characters.
Regular expression — delimited by slashes
Host — an IP address in dotted decimal format enclosed in brackets or a host name
Interface address, network address — an IP address with mask, enclosed in brackets
Socket — a host and a port number
Enumeration — a set of names representing integer constants
List — a sequence of values of a basic type, separated by commas and enclosed in braces. Lists can be nested.
Set — a set of values of a basic type. Syntax is similar to lists with additional features—ranges, exclusion of members, and wildcards. Sets of some types allow special members, e.g., regular expressions in a set of strings or host addresses.
Important
In the GUI, the values must be entered including quoting characters, such as double quotes for strings and brackets for IP addresses.
We have introduced only the basic concepts of the Kernun UTM configuration
language. The complete definition of the language syntax can be found in
reference pages
configuration(7) and
cml(8). The semantics of the configuration is
defined by the meaning of individual sections, items, and elements. Semantic rules
also define the subsections and items each section may contain.
There are constraints, e.g. that the existence of a configuration node
requires or forbids the existence of another node. The set of possible values of
a configuration element can be limited. A section or item can be repeatable
(can occur several times, in the case of sections with different
names), or non-repeatable (cannot occur more than once;
non-repeatable sections do not have names). For example, in Figure 4.1, “Tree structure of the configuration”, the named sections system and
interface are repeatable, whereas the section
crontab is non-repeatable. The semantics of the configuration is
described comprehensively in section 5 of the reference pages (in the appendix of
this handbook or in manual pages displayed using the
man(1)) command.
[17] They are mainly
proxy configuration files and some system configuration files, e.g.,
/etc/rc.conf.