Kernun UTM can cooperate with the SpamAssassin antispam software to reject or mark spam. Three more methods can be used in addition to the SpamAssassin protection: black-listing (rejection of mail from senders with addresses listed in an external database), white-listing (authorisation of the sender on his or her domain server) and grey-listing (an automatic method based on a local database). We will discuss the configuration of antispam first, and then briefly describe the individual methods in the next sub-chapter.
Like the Dr.WEB or ClamAV antivirus programs, you can install
SpamAssassin either directly on Kernun UTM or on any other machine
connected via the network. The antispam configuration in Kernun UTM is
analogous to the antivirus configuration. We define the
antispam section on the system level,
and we reference this section in the mail processing proxies
(smtp-proxy, pop3-proxy, and
imap4-proxy).
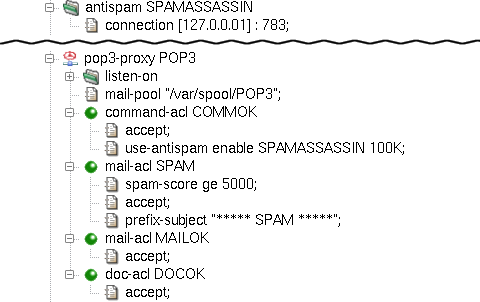
We can use the results of the antispam check in the spam-score item[38] in the mail-acl section of the spam-checked proxy.
Having configured the SPAMASSASSIN section, we
now reference it in the proxies. We replace the item no-mail-scanning (in the
command-acl section) with use-antispam enable SPAMASSASSIN 100K.
Tip
Antispam checking is a very demanding operation, and typical spam mails are quite small. You may therefore want to check only messages below a certain limit size, such as 100 kB in our case.
Because we deleted the no-mail-scanning item, Kernun UTM will search for
matching mail-acl and doc-acl sections and we must
therefore create them. (Otherwise, Kernun UTM's default reaction would be to
reject the mail.) We create a mail-acl
section that will mark spammed e-mails, but deliver them to the recipient(s).
We do so by adding an acl condition spam-score
and setting it to accept e-mails with a spam score exceeding 5.0 (we use the relational
operator ge; the Kernun UTM spam score of 5000 corresponds to SpamAssassin's
score of 5.0 multiplied by 1000). We specify that such messages will be accepted, but define
a prefix-subject item that adds a text prefix to their subject.
Finally, we add accepting mail-acl and
doc-acl and we get the configuration shown in
Figure 5.63, “Antispam protection for POP3 proxy”.
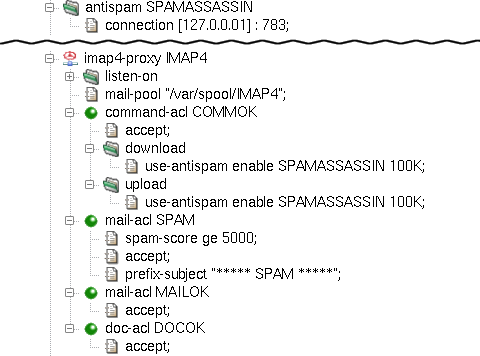
Analogously, we can add antispam support to the IMAP4 proxy.
We add the use-antispam items to both download
and upload sections, and then create the mail-acl and
doc-acl sections. Figure 5.64, “Antispam protection for IMAP4 proxy” shows the antispam
configuration of imap4-proxy.
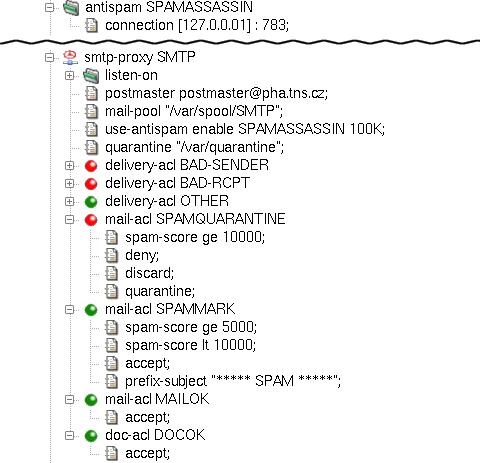
The configuration of smtp-proxy is, again,
similar to the previous cases, only this time we define the use-antispam item
right inside the proxy. In this example we show how to deny mails with too high a spam score
and store them in quarantine on the server. We do so by specifying a quarantine
item in the proxy and setting it to the path of the quarantine directory.
Remember that we work under a chrooted environment, so we need to create that directory
inside the chroot (in our example, /usr/local/kernun/root/var/quarantine).
We add a mail-acl SPAMQUARANTINE with items deny to
not deliver messages with SpamAssassin score exceeding 10, discard to not inform the sender
about the delivery failure and quarantine to place the mail into the quarantine directory.
Another mail-acl, SPAMMARK, is
used to pass e-mails with the score of 5-10, but mark it with a subject prefix.
The relevant part of the SMTP proxy configuration with antispam is shown in
Figure 5.65, “Antispam protection for SMTP proxy”.
The resulting configuration of mail proxies with antispam is available in the
/usr/local/kernun/conf/samples/cml/antispam.cml sample file.
For more information on antispam configuration, see the mod-antispam(5) manual page.
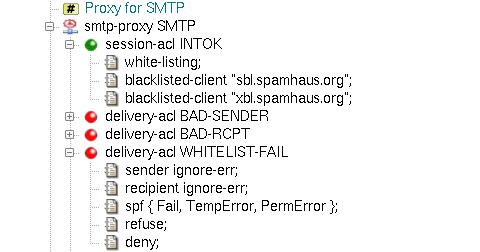
Kernun UTM's smtp-proxy provides
configurable client identity checking as protection against unsolicited
mail. White-listing implemented in Kernun UTM is based on the Sender
Policy Framework (http://www.openspf.org), which checks if the
sender is allowed in the sender policy of the return path domain and thus
authorizes the sender. After inserting a white-listing item into
session-acl, the result of the matching can be used in the delivery-acl
section using the spf condition.
On the other hand, the black-listing method checks the sender's address against an external database of
forbidden IP addresses. The sender's presence in such a database (for example http://www.spamhaus.org)
means that the e-mail is denied during the session-acl phase.
The configuration of black- and white-listing is depicted in Figure 5.66, “White- and black-listing for SMTP proxy”. The list of the main
black-listing databases is defined in /usr/local/kernun/conf/samples/include/smtp-blacklist.cml.
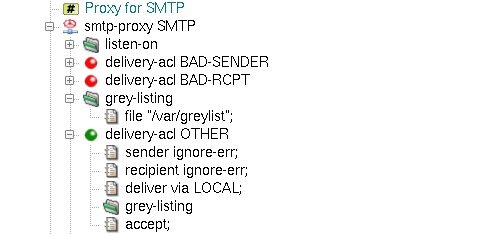
Grey-listing is a mail-filtering method that does not rely on any external database or domain information. Instead,
it creates its own database of triplets (sender IP, sender e-mail address, recipient e-mail address) and behaves according
to the state of triplet in the database. New e-mail is saved as blocked and a temporary error
answer is sent to the sender. If the sender tries to redeliver the mail within a predefined period (e.g., after some time,
but not too late), the state of the triplet changes to granted and all mail with the same
triplet will then be passed without any blocking time. The grey-listing method is configured by the
grey-listing section in the delivery-acl, and the grey-listing
section with a path item set to the filename of the grey-listing database in smtp-proxy.
A sample grey-listing configuration is shown in Figure 5.67, “Grey-listing for SMTP proxy”. For more detailed information about
the method, see the description of the
triplicator(1) tool.
[38] In fact, the score returned by SpamAssassin is multiplied by 1000, because the Kernun UTM configuration does not handle floats. This feature also allows the future compatibility with other antispam software.