Kernun supports IPsec in the transport and tunnel modes, using the ESP protocol. In the transport mode, Kernun requires a tunnel (GIF or GRE) interface and uses IPsec to encrypt the encapsulated traffic passed via this interface. In the tunnel mode, IPsec encrypts traffic between the specified networks. IPsec in Kernun consists of several parts, represented by components in GKAT. IPsec packets are handled by the operating system kernel according to the SPD (Security Policy Database) and SAD (Security Association Database). The SPD entries for individual IPsec tunnels are controlled by the ipsec Kernun components. Security associations are created by ISAMKP daemon Racoon, presented also as a separate component.
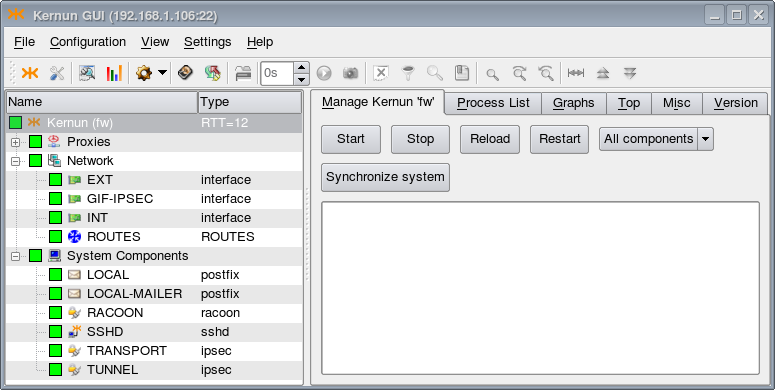
A GKAT window with IPsec-related components is depicted
in Figure 5.98, “IPsec components in a GKAT window”. There is a GIF tunnel network interface
called GIF-IPSEC, which is used by the IPsec tunnel represented by
the TRANSPORT component. Another IPsec tunnel, the
TUNNEL component, uses IPsec in the tunnel mode (without
a related tunnel interface). The RACOON component is the ISAKMP
daemon.
The examples of IPsec configuration described here are available in the sample
configuration file
/usr/local/kernun/conf/samples/cml/ipsec.cml.
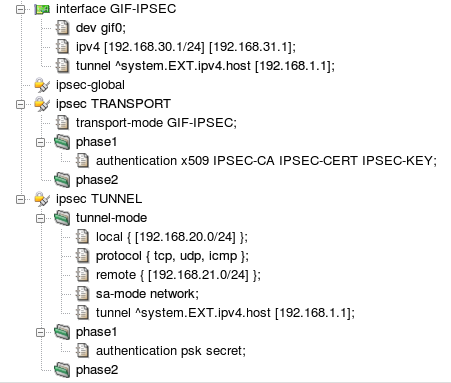
The resulting IPSec configuration in both modes is shown in Figure 5.99, “IPsec configuration”. When applied, IPsec-related components
GIF-IPSEC, RACOON,
TRANSPORT, and TUNNEL will be created
and become visible in GKAT (see Figure 5.98, “IPsec components in a GKAT window”). For
IPsec in the transport mode, the configuration contains the tunnel interface
GIF-IPSEC. Its configuration section defines the
interface device name, local and remote logical IP addresses, and the
tunnel addresses (the physical IP addresses used for the encapsulation of
tunneled packets). Section ipsec-global can contain
global parameters of the ISAKMP daemon. There is a section for each IPsec
tunnel. Section ipsec TRANSPORT configures IPsec in
the transport mode for encryption of packets travelling via interface
GIF-IPSEC. The authentication utilizes X.509 certificates.
Other ISAKMP phase 1 and phase 2 parameters have the default
values. Section ipsec TUNNEL sets up IPsec in the
tunnel mode. It is not related to any network interface, hence the
networking parameters — local, remote, and tunnel (physical)
addresses, set of protocols handled by IPsec, and security association
mode — are defined inside the ipsec section.
A pre-shared secret key for authentication is specified. Again, the remaining
ISAKMP parameters have the default values.