The Kernun UTM boot manager is located on the system disk. It is installed during the initialization of the system performed by the standalone installer. Depending on the partitioning scheme, there is either ZFS or LEGACY (UFS) boot manager.
The Kernun GUI or the command line bootmgr(8) utility can be used to change partition labels, enable and disable booting from individual partitions, and set whether the default boot partition is fixed, or is always changed to the last booted partition.
There is a default partition selected for boot, which boots
automatically. It is also possible to select another partition during the
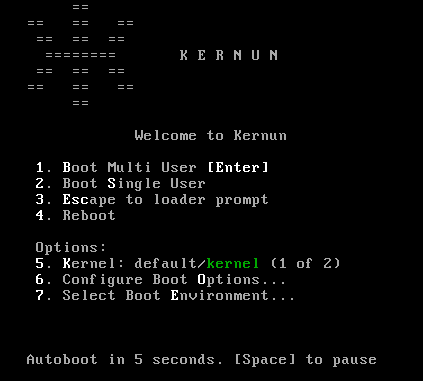
boot sequence. The boot manager displays the menu as shown in Figure 2.1, “ZFS boot manager screen 1”. Press option 7 to select the
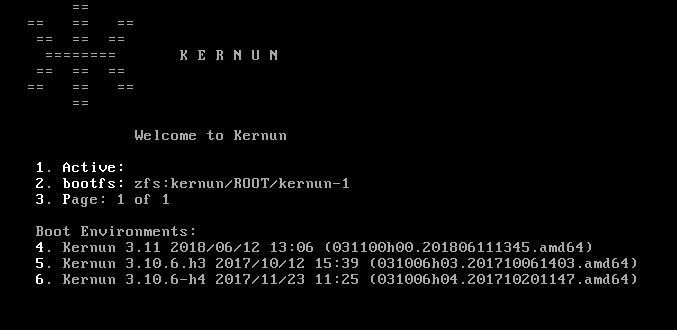
boot partition. Another menu is displayed (see Figure 2.2, “ZFS boot manager screen 1”).
In this menu, press the number that corresponds to the system to be booted. For
example, press option 5<Enter> to boot the Kernun 3.10.6.h3.
The boot manager displays labels of up to three system
partitions and allows selection of the partition to boot from by pressing
F1, F2, or
F3.
F1 Kernun 3.0 2008/10/01 07:36 (030000h00.200809241501.i386) F2 Kernun 3.0 2008/10/18 05:21 (030000h00.200810170852.i386) F3 Kernun 3.0.1 2008/11/15 07:22 (030001h00.200811142135.i386) Default: F2
If no option is selected, the default one is chosen automatically after a timeout.
Anybody with physical access to the Kernun UTM console may select a system partition to boot from, boot a different kernel or kernel modules, or boot to the single user mode and access the system without a password. If the system console is not physically secure, the following actions can be done to protect the system against unauthorized access:
Disable boot device selection in the BIOS (for example, by setting a BIOS password).
Enable only the desired system partition in the boot manager (using bootmgr(8)).
Add line “
-n” to/boot.config. This prevents interrupting the boot process in the stages one and two.#printf -- '-n\n' > /boot.configProtect the loader with a password by adding a password line to
/boot/loader.conf. Make the file readable only by root.#echo 'password="SECRET"' >> /boot/loader.conf#chmod go-rw /boot/loader.confForce verification of the root password as a condition for entering the single user mode. Locate the line beginning with “
console” in/etc/ttysand change its last word to “insecure”.