Kernun UTM provides a generic proxy for handling application protocols based on UDP. Its philosophy is similar to the generic TCP proxy, which is used for the HTTPS and SSH protocols in the initial configuration, as described in Section 2.9, “HTTPS and SSH Proxy”. The proxy waits on one or more ports, transparently or non-transparently, for datagrams from clients. Although UDP is a stateless protocol, the UDP proxy defines logical sessions that group together related datagrams. See udp-proxy(8).
We will demonstrate the UDP proxy on the DNS protocol. It is one of typical applications of the UDP proxy[28]. Kernun UTM provides the DNS proxy (refer to Figure 4.11, “DNS Proxy”), which is a better choice for accessing DNS servers in the Internet, because it performs thorough checks of the protocol. However, if Kernun UTM connects two trusted internal networks and clients in one of them send DNS requests to a server in the other, the use of the UDP proxy may be sufficient.
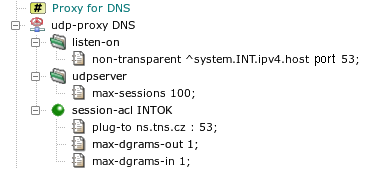
The DNS proxy in the sample configuration in Figure 5.37, “UDP proxy
” was replaced by the UDP proxy. It listens on the
internal network interface on the DNS UDP port 53 non-transparently. The item
max-sessions in section udpserver limits
the maximum number of logical sessions that can be handled by the proxy
simultaneously. All DNS requests from the internal network are accepted by
global acl INTOK. This ACL is extended in the proxy by
the plug-to item, which forwards all requests to a single DNS
server. As DNS is a request-reply protocol, we define that each logical
session contains at most one request (client to server) and one response
(server to client) datagram.
The setup described in this section can be tested by specifying in
plug-to a DNS server that accepts and recursively solves
requests from Kernun UTM. The client machines must be configured to use
Kernun UTM as their DNS server.